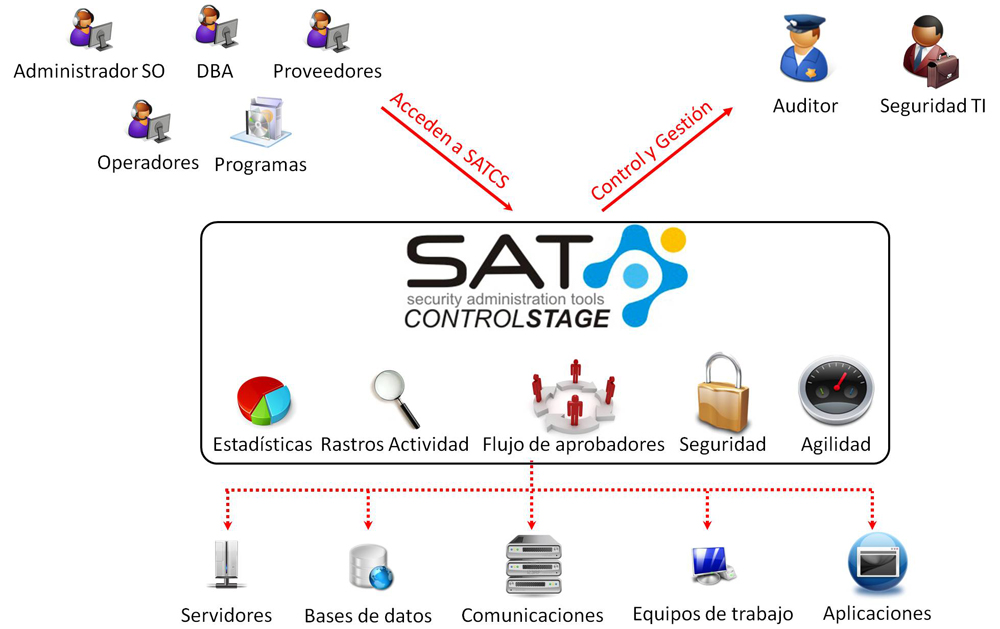
Stage SAT Control is a tool to manage passwords for privileged users automatically or manually on multiple platforms without the need for agents.
Supported platforms: UNIX, Linux, AIX, Solaris, Windows, Active Directory, iSeries, zSeries, SQL, Oracle, and other communication equipment ...